In the first installment in this series, we answered the question, What is the AFC test? In the second installment we discussed when to apply the AFC test. In this installment, we consider what the AFC test reveals.
Consider the following example, which illustrates the AFC test’s ability to reveal hidden similarities in the structure, sequence, and organization of two programs.
Company A creates a Java program for baking pies. This simple program is named “Bake Pie,” and Company A holds a registered copyright for “Bake Pie.”
Company B also creates a Java program for baking pies. This program is named “Perfect Pie.” The “Perfect Pie” program was written by a former employee of Company A, and evidence indicates that the employee took a thumb drive containing the “Bake Pie” code with him after his termination. Company A sues Company B and former employee for copyright infringement, and code for both programs is produced for experts to review.
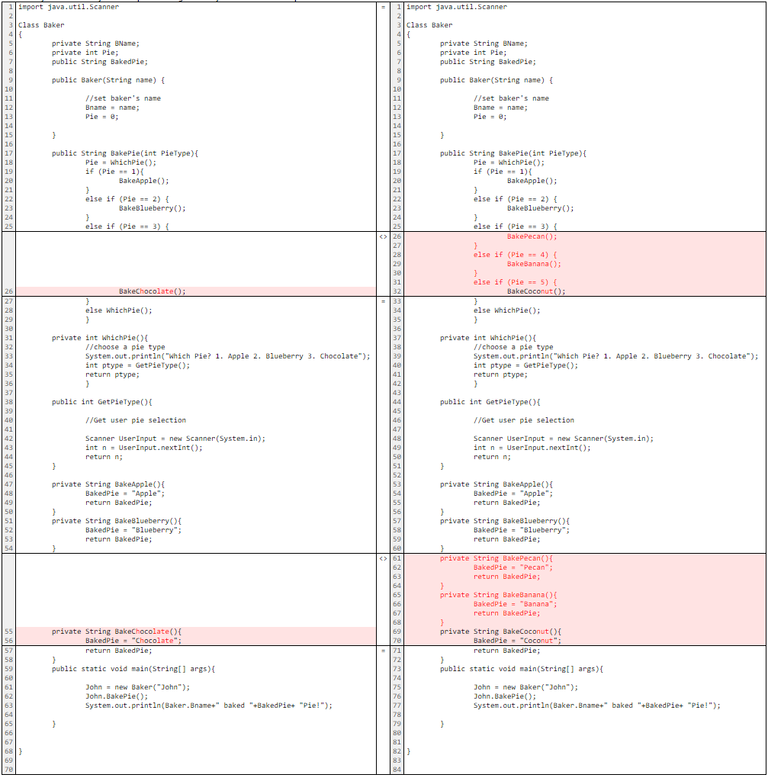
An expert must first determine whether literal copying occurred, perhaps by using text comparison software to directly compare the programs line-by-line. Were an expert to use a text comparison software, like Beyond Compare1, to examine the “Bake Pie” and “Perfect Pie” programs, the result of such a comparison might look something like the screenshot below, with “Bake Pie” on the left and “Perfect Pie” on the right. Lines in white match exactly, while lines highlighted in red do not match.
Most of the programs’ lines match exactly, indicating that literal copying occurred. A situation in which literal copying occurred may not require an expert to perform the AFC test. But perhaps, instead of creating “Perfect Pie” in Java, the language used in “Bake Pie,” Company B creates it in the Visual Basic .NET language.
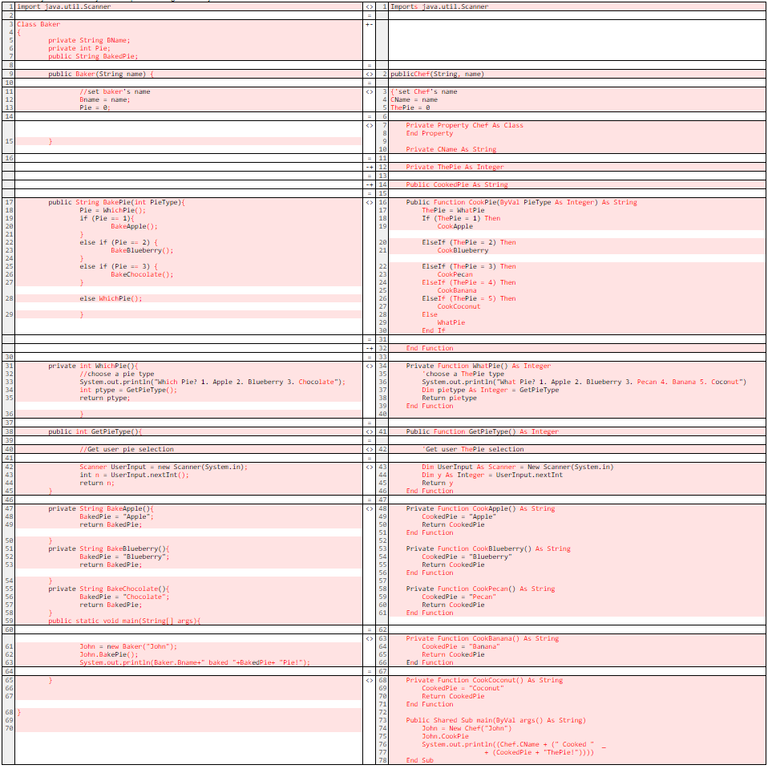
The below screenshot illustrates what happens when an expert compares the two programs using Beyond Compare.
One cannot immediately determine whether one program was copied from the other by merely looking at the literal code, as no text matches exactly, and the programs share only blank lines. This is a direct result of “Perfect Pie” being written in an entirely different programming language than “Bake Pie.”
However, these two programs still may be similar in other ways.2
While the text comparison software indicates that “Pefect Pie” did not copy source code directly from “Bake Pie,” the two programs’ variable names, method names, and program sequence are suspiciously similar, raising the question of whether non-literal elements of “Perfect Pie” were copied from “Bake Pie.” How might an expert determine whether “Perfect Pie” exhibits similarity to “Bake Pie” with regard to structure, sequence, and organization?
In this example, assume that the employee in question had access to the original protected work of Company A. This fact allows us to analyze the two programs for evidence of non-literal copying. One method of conducting such an analysis is to apply the AFC test. For the purposes of this example, we abstract each program into simple modules, with a module for each function. Assume as well for this example that after applying various filters (e.g., legal doctrines, industry-specific requirements, etc.), we have concluded that nothing needs to be filtered out of the programs, as they contain only protectable code.
Now that the abstraction and filtration steps are complete, we can compare the programs; one way to do this is by examining the programs’ “control flow” through the modules.
The way a program gets from start to finish is referred to as its control flow. A computer program that needs to accomplish a specific task can do so using a variety of different control flow structures, and a programmer’s decision to design a program’s control flow one way instead of another way may arguably be protectable expression.
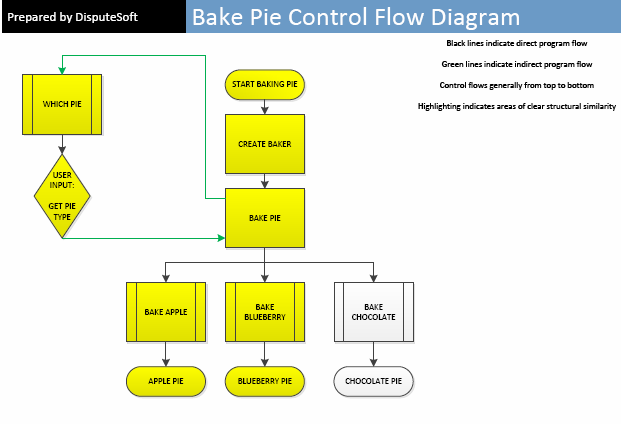
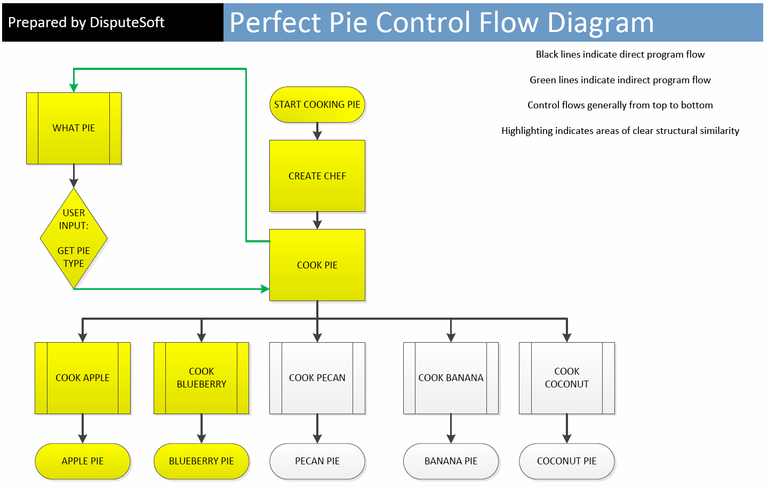
Examining control flow can reveal similarities in two programs’ structure, sequence and organization that may have remained hidden from other analyses. Below are two control flow diagrams, one for “Bake Pie” and one for “Perfect Pie,” with similarities in structure, sequence, and organization highlighted in yellow.
Although the “Perfect Pie” program contains three pies (Pecan, Banana, and Coconut) that “Bake Pie” does not, and the “Bake Pie” program contains one pie (Blueberry) that “Perfect Pie” does not, the diagrams show that the structure, sequence, and organization of “Perfect Pie” is very similar to that of “Bake Pie.” Both start in the same way, generate a person to create the pie, create the pie by getting user input, call the function to create the pie, and generate a pie as the end result.
Such similarity suggests that non-literal elements of “Perfect Pie” were copied from “Bake Pie.” Had “Perfect Pie” accomplished the same task as “Bake Pie” by ordering the steps of its control flow differently or by employing completely different procedures, the non-literal elements of the two programs may have been different enough to conclude that protected expression was not copied from the other.
The AFC test can reveal material similarities between programs that may have otherwise remained hidden.
Software experts use the process of abstracting programs into modules, filtering out non-protectable elements, and comparing the control flow of the programs to come to an opinion regarding whether two programs that differ literally are still substantially similar.
This is especially necessary when a party suspects that protected code was copied and translated into a different programming language or otherwise used as the basis for creating a competing program.
This is where software experts can be vital to potential software copyright infringement cases where the issue of protected code is in doubt.
Josh Siegel
Josh Siegel has substantial experience analyzing copyright, patent, and trade secret cl…
T.J. Wolf
Since joining DisputeSoft in 2016, T.J. Wolf has consulted for clients on a variety of…